Summer Properties, Hashes, and Cyber Security
Here is a gem of a program: Summer Properties. This program adds a new tab to the the File Properties dialog in Windows. Inside this tab are the MD5 and SHA1 hash codes (and two others).
So what is a hash–and what does MD5 mean? And what are these codes useful for? This post will give a surface-level look into a very complicated topic.
An example is probably the best way to explain: every time you type a password into Facebook, Facebook’s computer system checks to see if the password you entered is correct (Note: I doubt Facebook uses the exact methods described below; I’m just using them as an example to illustrate the general idea). Now, the simplest way to do this would be for Facebook to have a database of all the passwords with their corresponding usernames (or email addresses). That works well… until someone hacks into the computer system. Suddenly, the hacker has access to all of the passwords!
To work around this problem, most servers nowadays don’t store the passwords of their users. Instead, they store a password hash. So what is a hash? A hash is a sequence of letters and numbers that looks like this:
b11ef87c5f667b55b15303311f6c4b7d
This sequence is produced using a hashing process, in this case Message Digest 5 (MD5). Another popular process is Secure Hash Algorithm 1 (SHA1). These processes are designed so that they produce a unique, repeatable sequence of figures for any given line of text or file.
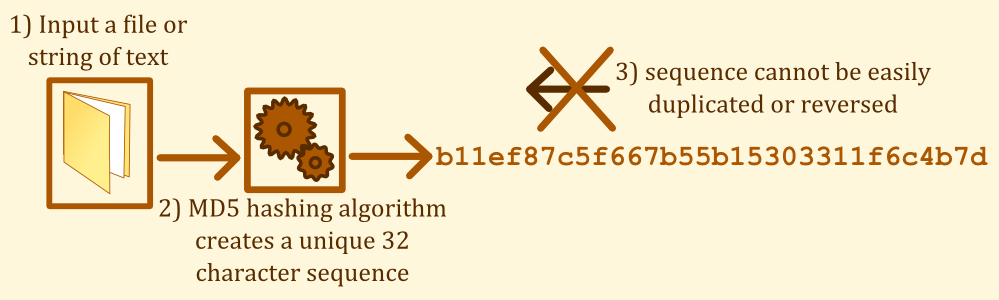 The algorithms are designed so that if a single byte of a file changes, the hash value will change. Also, these algorithms are designed so that they cannot be reversed–it is very difficult (nigh impossible) to determine what the original input was given only the MD5 hash value.
The algorithms are designed so that if a single byte of a file changes, the hash value will change. Also, these algorithms are designed so that they cannot be reversed–it is very difficult (nigh impossible) to determine what the original input was given only the MD5 hash value.
So what does this have to do with logging into Facebook? Well, instead of storing unprotected passwords in a list–since they could be stolen–Facebook’s servers instead save the hash values of the passwords. That way, if the server is hacked, the hackers won’t have easy access to user accounts–all they’ll have is strings of random letters and numbers that don’t give them access to anything.
The beauty of this system is that when you type in your password on the log in screen, the server calculates the hash value for your password and then checks it to make sure it’s the same as the hash value for your account in its database. If the values match, then your password must be valid and you become logged in.
Conclusion
So back to Summer Properties. This add-on will calculate MD5 and SHA1 values for files. This is handy because many websites include pre-calulated hash values for their products on their downloads page. After you download a file, you can check to make sure the calculated hash value in Summer Properties corresponds with the hash value listed on the downloads page. If the values match, all is well. If not, then something malicious may be attached to the file or the file may have been corrupted during download.
While I don’t check every file I download, I do like to have the option of checking hash values, especially when I’m downloading files from sites with which I’m unfamiliar (open-source software sites, Linux sites, etc.). Summer Properties is a great utility for this!